Global Intelligent Threat Security Market Size, Share & Trends Analysis Report, Forecast Period, 2023-2031
Report ID: MS-1502 | IT and Telecom | Last updated: Jul, 2024 | Formats*:
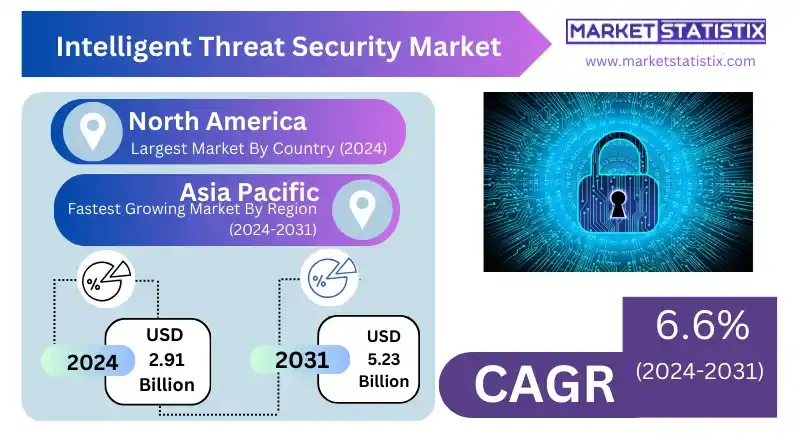
Intelligent Threat Security Report Highlights
| Report Metrics | Details |
|---|---|
| Forecast period | 2019-2031 |
| Base Year Of Estimation | 2023 |
| Growth Rate | CAGR of 6.6% |
| Key Market Players |
|
| By Region |
|
Intelligent Threat Security Market Leading Players
The key players profiled in the report are SecLytics (US), EclecticIQ (Netherlands), Cyware, Forcepoint (US), LookingGlass (US), LogRhythm, ThreatConnect (US), Fortinet (US), Anomali (US), SOCRadar (US), Keepnet Labs (UK)(US), Recorded Future (US), Optiv (US), IBM (US), Cisco (US), Trend Micro (Japan), McAfee (US), Mimecast (UK), VMware (US), Technology (US), Broadcom (US), NSFOCUS, AT&T (US), Check Point (Israel), DXC (US), CrowdStrike (US), Juniper Networks (US), Cymulate (US), CYFIRMA (Singapore)Growth Accelerators
Increasing cyber threats Strong among the forces are the growing sophistication and frequency of cyber-attacks. Traditional measures in security are failing to keep up with the development of the tactics of cybercriminals. Intelligent threat security solutions, with inherent learning and adaptability, bring a strong and potent countermeasure. This understanding is leading to a realization of the fact that organizations are increasingly realizing the need for enhanced solutions to toughen their defences and stay one step ahead of the game. The other big driver is the cybersecurity skills gap. There is a phenomenal shortage of quality manpower in management and the analysis of security-based threats. Intelligent threat security solutions can automate many of these tasks, thus freeing security professionals to really focus on more strategic and incident response-related initiatives. This then allows organizations to be responsive to their security needs even when they have minimal human resources.Intelligent Threat Security Market Segmentation analysis
The Global Intelligent Threat Security is segmented by Application, and Region. . The Application segment categorizes the market based on its usage such as Security Information and Event Management, Business Continuity Planning and Management, Government Risk and Compliance. Geographically, the market is assessed across key Regions like North America(United States.Canada.Mexico), South America(Brazil.Argentina.Chile.Rest of South America), Europe(Germany.France.Italy.United Kingdom.Benelux.Nordics.Rest of Europe), Asia Pacific(China.Japan.India.South Korea.Australia.Southeast Asia.Rest of Asia-Pacific), MEA(Middle East.Africa) and others, each presenting distinct growth opportunities and challenges influenced by the regions.Competitive Landscape
Mergers and Partnerships: Traditional players in the security market are really doubling down on this trend by infusing AI and ML technologies into their existing solutions, and a few are even in the phase of acquiring niche players that provide advanced threat intelligence capabilities. With this trend, known, large, established vendors can begin leveraging their brand value, recognition, and wide distribution presence within the market to grow their share in the intelligent security segment. Focus on specialisation and differentiation: Some may offer end-to-end security platforms with all the intelligent threat security features required, while others may specialise in one sub-domain, such as endpoint security or network traffic analysis. This specialisation ability allows them to clearly differentiate themselves and serve the diversified needs arising from thousands of market segments. To stay competitive, vendors are in continuous development of unique capabilities.Challenges In Intelligent Threat Security Market
Implementation and Integration Complexity: Intelligent threat security solutions often require complex configurations and have to be integrated with already established security infrastructures. This potentially bears a high cost of implementation—more so for organisations lacking adequate skills and experience in IT, AI, and machine learning. In addition, all these intelligent solutions are going to produce a significantly high number of alerts that require experienced security staff for their enjoyment and prioritization. To fix that, the vendors have turned their focus back to user-friendly interfaces and the degree of automation around deployments and ongoing management. Data Quality and Bias in AI Algorithms: The accuracy and overall efficiency of intelligent threat security solutions relate to the quality and quantity of data with which the artificial intelligence and machine learning models are trained. Insufficiently or mistakenly collected data relies on will lead to either false positives or false negatives. There is also the risk that these algorithms have embedded bias that merely amplifies the bias of the training data.Key Target Audience
Large Enterprises with High Value Assets: Some would include financial institutions, health care facilities, and key infrastructure operators. They have a huge value of assets at their disposal, normally with sensitive data, prompting attacks with the intent of cyberespionage. Hence, they will require highly efficient security that does not merely detect but also responds to sophisticated zero-day attacks. In that case, AI and machine learning will confer advanced detection and intelligence capacities to keep pace with changing threats.,, , Cyber-Savvy Businesses Both Large and Small: All companies are starting to recognize the importance of strong cybersecurity to protect them from threatening elements. With the rise in cyber-attacks that can bring financial harm to companies and tarnish the image of an organization, there is also an increasing demand for sharp threat security solutions that can offer proper protection without overburdening big security staff. Automated threat detection and analysis capabilities make them a valuable option for organizations with limited security resources.Merger and acquisition
A good example would fit when Intel acquired McAfee in 2021. What the purchase really does is blend McAfee's existing endpoint security portfolio with Intel's hardware and AI capabilities into an intelligent threat security platform informed by AI for an elevated level of threat detection and prevention across endpoints. Another big thing came in the proximity of 2020, when Broadcom acquired the Symantec enterprise security business. In the past, Symantec was a powerhouse in the traditional security market, so this acquisition really put Symantec's security offerings on top of Broadcom's existing smorgasbord of AI and machine learning expertise, making it a fiercer competitor in the intelligent threat security landscape.- 1.1 Report description
- 1.2 Key market segments
- 1.3 Key benefits to the stakeholders
2: Executive Summary
- 2.1 Intelligent Threat Security- Snapshot
- 2.2 Intelligent Threat Security- Segment Snapshot
- 2.3 Intelligent Threat Security- Competitive Landscape Snapshot
3: Market Overview
- 3.1 Market definition and scope
- 3.2 Key findings
- 3.2.1 Top impacting factors
- 3.2.2 Top investment pockets
- 3.3 Porter’s five forces analysis
- 3.3.1 Low bargaining power of suppliers
- 3.3.2 Low threat of new entrants
- 3.3.3 Low threat of substitutes
- 3.3.4 Low intensity of rivalry
- 3.3.5 Low bargaining power of buyers
- 3.4 Market dynamics
- 3.4.1 Drivers
- 3.4.2 Restraints
- 3.4.3 Opportunities
4: Intelligent Threat Security Market by Application / by End Use
- 4.1 Overview
- 4.1.1 Market size and forecast
- 4.2 Security Information and Event Management
- 4.2.1 Key market trends, factors driving growth, and opportunities
- 4.2.2 Market size and forecast, by region
- 4.2.3 Market share analysis by country
- 4.3 Business Continuity Planning and Management
- 4.3.1 Key market trends, factors driving growth, and opportunities
- 4.3.2 Market size and forecast, by region
- 4.3.3 Market share analysis by country
- 4.4 Government Risk and Compliance
- 4.4.1 Key market trends, factors driving growth, and opportunities
- 4.4.2 Market size and forecast, by region
- 4.4.3 Market share analysis by country
5: Intelligent Threat Security Market by Component
- 5.1 Overview
- 5.1.1 Market size and forecast
- 5.2 Solution
- 5.2.1 Key market trends, factors driving growth, and opportunities
- 5.2.2 Market size and forecast, by region
- 5.2.3 Market share analysis by country
- 5.3 Services
- 5.3.1 Key market trends, factors driving growth, and opportunities
- 5.3.2 Market size and forecast, by region
- 5.3.3 Market share analysis by country
- 5.4 Professional Services
- 5.4.1 Key market trends, factors driving growth, and opportunities
- 5.4.2 Market size and forecast, by region
- 5.4.3 Market share analysis by country
- 5.5 Managed Services
- 5.5.1 Key market trends, factors driving growth, and opportunities
- 5.5.2 Market size and forecast, by region
- 5.5.3 Market share analysis by country
6: Intelligent Threat Security Market by Deployment mode
- 6.1 Overview
- 6.1.1 Market size and forecast
- 6.2 Cloud
- 6.2.1 Key market trends, factors driving growth, and opportunities
- 6.2.2 Market size and forecast, by region
- 6.2.3 Market share analysis by country
- 6.3 On-premises
- 6.3.1 Key market trends, factors driving growth, and opportunities
- 6.3.2 Market size and forecast, by region
- 6.3.3 Market share analysis by country
7: Intelligent Threat Security Market by Organization size
- 7.1 Overview
- 7.1.1 Market size and forecast
- 7.2 Large Enterprises
- 7.2.1 Key market trends, factors driving growth, and opportunities
- 7.2.2 Market size and forecast, by region
- 7.2.3 Market share analysis by country
- 7.3 SMEs
- 7.3.1 Key market trends, factors driving growth, and opportunities
- 7.3.2 Market size and forecast, by region
- 7.3.3 Market share analysis by country
8: Intelligent Threat Security Market by Region
- 8.1 Overview
- 8.1.1 Market size and forecast By Region
- 8.2 North America
- 8.2.1 Key trends and opportunities
- 8.2.2 Market size and forecast, by Type
- 8.2.3 Market size and forecast, by Application
- 8.2.4 Market size and forecast, by country
- 8.2.4.1 United States
- 8.2.4.1.1 Key market trends, factors driving growth, and opportunities
- 8.2.4.1.2 Market size and forecast, by Type
- 8.2.4.1.3 Market size and forecast, by Application
- 8.2.4.2 Canada
- 8.2.4.2.1 Key market trends, factors driving growth, and opportunities
- 8.2.4.2.2 Market size and forecast, by Type
- 8.2.4.2.3 Market size and forecast, by Application
- 8.2.4.3 Mexico
- 8.2.4.3.1 Key market trends, factors driving growth, and opportunities
- 8.2.4.3.2 Market size and forecast, by Type
- 8.2.4.3.3 Market size and forecast, by Application
- 8.2.4.1 United States
- 8.3 South America
- 8.3.1 Key trends and opportunities
- 8.3.2 Market size and forecast, by Type
- 8.3.3 Market size and forecast, by Application
- 8.3.4 Market size and forecast, by country
- 8.3.4.1 Brazil
- 8.3.4.1.1 Key market trends, factors driving growth, and opportunities
- 8.3.4.1.2 Market size and forecast, by Type
- 8.3.4.1.3 Market size and forecast, by Application
- 8.3.4.2 Argentina
- 8.3.4.2.1 Key market trends, factors driving growth, and opportunities
- 8.3.4.2.2 Market size and forecast, by Type
- 8.3.4.2.3 Market size and forecast, by Application
- 8.3.4.3 Chile
- 8.3.4.3.1 Key market trends, factors driving growth, and opportunities
- 8.3.4.3.2 Market size and forecast, by Type
- 8.3.4.3.3 Market size and forecast, by Application
- 8.3.4.4 Rest of South America
- 8.3.4.4.1 Key market trends, factors driving growth, and opportunities
- 8.3.4.4.2 Market size and forecast, by Type
- 8.3.4.4.3 Market size and forecast, by Application
- 8.3.4.1 Brazil
- 8.4 Europe
- 8.4.1 Key trends and opportunities
- 8.4.2 Market size and forecast, by Type
- 8.4.3 Market size and forecast, by Application
- 8.4.4 Market size and forecast, by country
- 8.4.4.1 Germany
- 8.4.4.1.1 Key market trends, factors driving growth, and opportunities
- 8.4.4.1.2 Market size and forecast, by Type
- 8.4.4.1.3 Market size and forecast, by Application
- 8.4.4.2 France
- 8.4.4.2.1 Key market trends, factors driving growth, and opportunities
- 8.4.4.2.2 Market size and forecast, by Type
- 8.4.4.2.3 Market size and forecast, by Application
- 8.4.4.3 Italy
- 8.4.4.3.1 Key market trends, factors driving growth, and opportunities
- 8.4.4.3.2 Market size and forecast, by Type
- 8.4.4.3.3 Market size and forecast, by Application
- 8.4.4.4 United Kingdom
- 8.4.4.4.1 Key market trends, factors driving growth, and opportunities
- 8.4.4.4.2 Market size and forecast, by Type
- 8.4.4.4.3 Market size and forecast, by Application
- 8.4.4.5 Benelux
- 8.4.4.5.1 Key market trends, factors driving growth, and opportunities
- 8.4.4.5.2 Market size and forecast, by Type
- 8.4.4.5.3 Market size and forecast, by Application
- 8.4.4.6 Nordics
- 8.4.4.6.1 Key market trends, factors driving growth, and opportunities
- 8.4.4.6.2 Market size and forecast, by Type
- 8.4.4.6.3 Market size and forecast, by Application
- 8.4.4.7 Rest of Europe
- 8.4.4.7.1 Key market trends, factors driving growth, and opportunities
- 8.4.4.7.2 Market size and forecast, by Type
- 8.4.4.7.3 Market size and forecast, by Application
- 8.4.4.1 Germany
- 8.5 Asia Pacific
- 8.5.1 Key trends and opportunities
- 8.5.2 Market size and forecast, by Type
- 8.5.3 Market size and forecast, by Application
- 8.5.4 Market size and forecast, by country
- 8.5.4.1 China
- 8.5.4.1.1 Key market trends, factors driving growth, and opportunities
- 8.5.4.1.2 Market size and forecast, by Type
- 8.5.4.1.3 Market size and forecast, by Application
- 8.5.4.2 Japan
- 8.5.4.2.1 Key market trends, factors driving growth, and opportunities
- 8.5.4.2.2 Market size and forecast, by Type
- 8.5.4.2.3 Market size and forecast, by Application
- 8.5.4.3 India
- 8.5.4.3.1 Key market trends, factors driving growth, and opportunities
- 8.5.4.3.2 Market size and forecast, by Type
- 8.5.4.3.3 Market size and forecast, by Application
- 8.5.4.4 South Korea
- 8.5.4.4.1 Key market trends, factors driving growth, and opportunities
- 8.5.4.4.2 Market size and forecast, by Type
- 8.5.4.4.3 Market size and forecast, by Application
- 8.5.4.5 Australia
- 8.5.4.5.1 Key market trends, factors driving growth, and opportunities
- 8.5.4.5.2 Market size and forecast, by Type
- 8.5.4.5.3 Market size and forecast, by Application
- 8.5.4.6 Southeast Asia
- 8.5.4.6.1 Key market trends, factors driving growth, and opportunities
- 8.5.4.6.2 Market size and forecast, by Type
- 8.5.4.6.3 Market size and forecast, by Application
- 8.5.4.7 Rest of Asia-Pacific
- 8.5.4.7.1 Key market trends, factors driving growth, and opportunities
- 8.5.4.7.2 Market size and forecast, by Type
- 8.5.4.7.3 Market size and forecast, by Application
- 8.5.4.1 China
- 8.6 MEA
- 8.6.1 Key trends and opportunities
- 8.6.2 Market size and forecast, by Type
- 8.6.3 Market size and forecast, by Application
- 8.6.4 Market size and forecast, by country
- 8.6.4.1 Middle East
- 8.6.4.1.1 Key market trends, factors driving growth, and opportunities
- 8.6.4.1.2 Market size and forecast, by Type
- 8.6.4.1.3 Market size and forecast, by Application
- 8.6.4.2 Africa
- 8.6.4.2.1 Key market trends, factors driving growth, and opportunities
- 8.6.4.2.2 Market size and forecast, by Type
- 8.6.4.2.3 Market size and forecast, by Application
- 8.6.4.1 Middle East
- 9.1 Overview
- 9.2 Key Winning Strategies
- 9.3 Top 10 Players: Product Mapping
- 9.4 Competitive Analysis Dashboard
- 9.5 Market Competition Heatmap
- 9.6 Leading Player Positions, 2022
10: Company Profiles
- 10.1 SecLytics (US)
- 10.1.1 Company Overview
- 10.1.2 Key Executives
- 10.1.3 Company snapshot
- 10.1.4 Active Business Divisions
- 10.1.5 Product portfolio
- 10.1.6 Business performance
- 10.1.7 Major Strategic Initiatives and Developments
- 10.2 EclecticIQ (Netherlands)
- 10.2.1 Company Overview
- 10.2.2 Key Executives
- 10.2.3 Company snapshot
- 10.2.4 Active Business Divisions
- 10.2.5 Product portfolio
- 10.2.6 Business performance
- 10.2.7 Major Strategic Initiatives and Developments
- 10.3 Cyware
- 10.3.1 Company Overview
- 10.3.2 Key Executives
- 10.3.3 Company snapshot
- 10.3.4 Active Business Divisions
- 10.3.5 Product portfolio
- 10.3.6 Business performance
- 10.3.7 Major Strategic Initiatives and Developments
- 10.4 Forcepoint (US)
- 10.4.1 Company Overview
- 10.4.2 Key Executives
- 10.4.3 Company snapshot
- 10.4.4 Active Business Divisions
- 10.4.5 Product portfolio
- 10.4.6 Business performance
- 10.4.7 Major Strategic Initiatives and Developments
- 10.5 LookingGlass (US)
- 10.5.1 Company Overview
- 10.5.2 Key Executives
- 10.5.3 Company snapshot
- 10.5.4 Active Business Divisions
- 10.5.5 Product portfolio
- 10.5.6 Business performance
- 10.5.7 Major Strategic Initiatives and Developments
- 10.6 LogRhythm
- 10.6.1 Company Overview
- 10.6.2 Key Executives
- 10.6.3 Company snapshot
- 10.6.4 Active Business Divisions
- 10.6.5 Product portfolio
- 10.6.6 Business performance
- 10.6.7 Major Strategic Initiatives and Developments
- 10.7 ThreatConnect (US)
- 10.7.1 Company Overview
- 10.7.2 Key Executives
- 10.7.3 Company snapshot
- 10.7.4 Active Business Divisions
- 10.7.5 Product portfolio
- 10.7.6 Business performance
- 10.7.7 Major Strategic Initiatives and Developments
- 10.8 Fortinet (US)
- 10.8.1 Company Overview
- 10.8.2 Key Executives
- 10.8.3 Company snapshot
- 10.8.4 Active Business Divisions
- 10.8.5 Product portfolio
- 10.8.6 Business performance
- 10.8.7 Major Strategic Initiatives and Developments
- 10.9 Anomali (US)
- 10.9.1 Company Overview
- 10.9.2 Key Executives
- 10.9.3 Company snapshot
- 10.9.4 Active Business Divisions
- 10.9.5 Product portfolio
- 10.9.6 Business performance
- 10.9.7 Major Strategic Initiatives and Developments
- 10.10 SOCRadar (US)
- 10.10.1 Company Overview
- 10.10.2 Key Executives
- 10.10.3 Company snapshot
- 10.10.4 Active Business Divisions
- 10.10.5 Product portfolio
- 10.10.6 Business performance
- 10.10.7 Major Strategic Initiatives and Developments
- 10.11 Keepnet Labs (UK)(US)
- 10.11.1 Company Overview
- 10.11.2 Key Executives
- 10.11.3 Company snapshot
- 10.11.4 Active Business Divisions
- 10.11.5 Product portfolio
- 10.11.6 Business performance
- 10.11.7 Major Strategic Initiatives and Developments
- 10.12 Recorded Future (US)
- 10.12.1 Company Overview
- 10.12.2 Key Executives
- 10.12.3 Company snapshot
- 10.12.4 Active Business Divisions
- 10.12.5 Product portfolio
- 10.12.6 Business performance
- 10.12.7 Major Strategic Initiatives and Developments
- 10.13 Optiv (US)
- 10.13.1 Company Overview
- 10.13.2 Key Executives
- 10.13.3 Company snapshot
- 10.13.4 Active Business Divisions
- 10.13.5 Product portfolio
- 10.13.6 Business performance
- 10.13.7 Major Strategic Initiatives and Developments
- 10.14 IBM (US)
- 10.14.1 Company Overview
- 10.14.2 Key Executives
- 10.14.3 Company snapshot
- 10.14.4 Active Business Divisions
- 10.14.5 Product portfolio
- 10.14.6 Business performance
- 10.14.7 Major Strategic Initiatives and Developments
- 10.15 Cisco (US)
- 10.15.1 Company Overview
- 10.15.2 Key Executives
- 10.15.3 Company snapshot
- 10.15.4 Active Business Divisions
- 10.15.5 Product portfolio
- 10.15.6 Business performance
- 10.15.7 Major Strategic Initiatives and Developments
- 10.16 Trend Micro (Japan)
- 10.16.1 Company Overview
- 10.16.2 Key Executives
- 10.16.3 Company snapshot
- 10.16.4 Active Business Divisions
- 10.16.5 Product portfolio
- 10.16.6 Business performance
- 10.16.7 Major Strategic Initiatives and Developments
- 10.17 McAfee (US)
- 10.17.1 Company Overview
- 10.17.2 Key Executives
- 10.17.3 Company snapshot
- 10.17.4 Active Business Divisions
- 10.17.5 Product portfolio
- 10.17.6 Business performance
- 10.17.7 Major Strategic Initiatives and Developments
- 10.18 Mimecast (UK)
- 10.18.1 Company Overview
- 10.18.2 Key Executives
- 10.18.3 Company snapshot
- 10.18.4 Active Business Divisions
- 10.18.5 Product portfolio
- 10.18.6 Business performance
- 10.18.7 Major Strategic Initiatives and Developments
- 10.19 VMware (US)
- 10.19.1 Company Overview
- 10.19.2 Key Executives
- 10.19.3 Company snapshot
- 10.19.4 Active Business Divisions
- 10.19.5 Product portfolio
- 10.19.6 Business performance
- 10.19.7 Major Strategic Initiatives and Developments
- 10.20 Technology (US)
- 10.20.1 Company Overview
- 10.20.2 Key Executives
- 10.20.3 Company snapshot
- 10.20.4 Active Business Divisions
- 10.20.5 Product portfolio
- 10.20.6 Business performance
- 10.20.7 Major Strategic Initiatives and Developments
- 10.21 Broadcom (US)
- 10.21.1 Company Overview
- 10.21.2 Key Executives
- 10.21.3 Company snapshot
- 10.21.4 Active Business Divisions
- 10.21.5 Product portfolio
- 10.21.6 Business performance
- 10.21.7 Major Strategic Initiatives and Developments
- 10.22 NSFOCUS
- 10.22.1 Company Overview
- 10.22.2 Key Executives
- 10.22.3 Company snapshot
- 10.22.4 Active Business Divisions
- 10.22.5 Product portfolio
- 10.22.6 Business performance
- 10.22.7 Major Strategic Initiatives and Developments
- 10.23 AT&T (US)
- 10.23.1 Company Overview
- 10.23.2 Key Executives
- 10.23.3 Company snapshot
- 10.23.4 Active Business Divisions
- 10.23.5 Product portfolio
- 10.23.6 Business performance
- 10.23.7 Major Strategic Initiatives and Developments
- 10.24 Check Point (Israel)
- 10.24.1 Company Overview
- 10.24.2 Key Executives
- 10.24.3 Company snapshot
- 10.24.4 Active Business Divisions
- 10.24.5 Product portfolio
- 10.24.6 Business performance
- 10.24.7 Major Strategic Initiatives and Developments
- 10.25 DXC (US)
- 10.25.1 Company Overview
- 10.25.2 Key Executives
- 10.25.3 Company snapshot
- 10.25.4 Active Business Divisions
- 10.25.5 Product portfolio
- 10.25.6 Business performance
- 10.25.7 Major Strategic Initiatives and Developments
- 10.26 CrowdStrike (US)
- 10.26.1 Company Overview
- 10.26.2 Key Executives
- 10.26.3 Company snapshot
- 10.26.4 Active Business Divisions
- 10.26.5 Product portfolio
- 10.26.6 Business performance
- 10.26.7 Major Strategic Initiatives and Developments
- 10.27 Juniper Networks (US)
- 10.27.1 Company Overview
- 10.27.2 Key Executives
- 10.27.3 Company snapshot
- 10.27.4 Active Business Divisions
- 10.27.5 Product portfolio
- 10.27.6 Business performance
- 10.27.7 Major Strategic Initiatives and Developments
- 10.28 Cymulate (US)
- 10.28.1 Company Overview
- 10.28.2 Key Executives
- 10.28.3 Company snapshot
- 10.28.4 Active Business Divisions
- 10.28.5 Product portfolio
- 10.28.6 Business performance
- 10.28.7 Major Strategic Initiatives and Developments
- 10.29 CYFIRMA (Singapore)
- 10.29.1 Company Overview
- 10.29.2 Key Executives
- 10.29.3 Company snapshot
- 10.29.4 Active Business Divisions
- 10.29.5 Product portfolio
- 10.29.6 Business performance
- 10.29.7 Major Strategic Initiatives and Developments
11: Analyst Perspective and Conclusion
- 11.1 Concluding Recommendations and Analysis
- 11.2 Strategies for Market Potential
Scope of Report
| Aspects | Details |
|---|---|
By Application |
|
By Component |
|
By Deployment mode |
|
By Organization size |
|
Report Licenses
Our Team

Frequently Asked Questions (FAQ):
What is the growth rate of Intelligent Threat Security Market?
+
-
What are the latest trends influencing the Intelligent Threat Security Market?
+
-
Who are the key players in the Intelligent Threat Security Market?
+
-
How is the Intelligent Threat Security } industry progressing in scaling its end-use implementations?
+
-
What product types are analyzed in the Intelligent Threat Security Market Study?
+
-
What geographic breakdown is available in Global Intelligent Threat Security Market Study?
+
-
How are the key players in the Intelligent Threat Security market targeting growth in the future?
+
-
What are the opportunities for new entrants in the Intelligent Threat Security market?
+
-
What are the major challenges faced by the Intelligent Threat Security Market?
+
-
What is the list of players included in the research coverage of the Intelligent Threat Security Market Study?
+
-

