Global Privileged Access Management (PAM) Solutions Market Size, Share & Trends Analysis Report, Forecast Period, 2023-2032
Report ID: MS-1954 | Chemicals And Materials | Last updated: Dec, 2024 | Formats*:
privileged access management (PAM) solutions Report Highlights
| Report Metrics | Details |
|---|---|
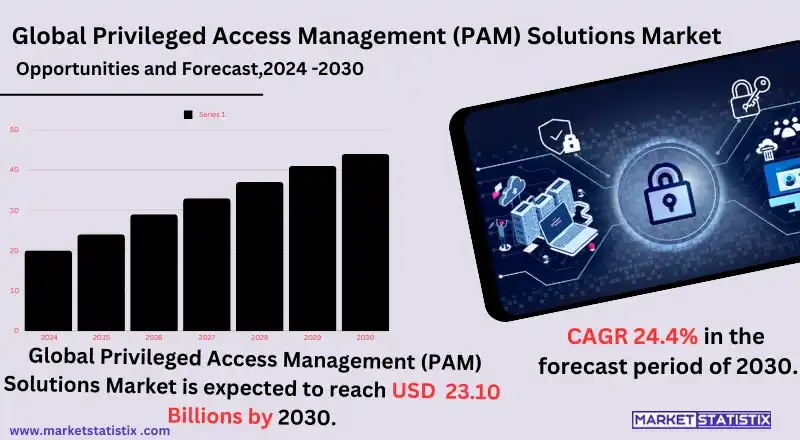
| Forecast period | 2019-2030 |
| Base Year Of Estimation | 2023 |
| Growth Rate | CAGR of 24.4% |
| Forecast Value (2030) | USD 23.10 billion |
| By Product Type | Software, Physical Appliance, Virtual Appliance |
| Key Market Players | BeyondTrust Corporation (U.S.), CyberArk Software Ltd. (U.S.), SecureAuth Corporation (U.S.), One Identity LLC (U.S.), Zoho Corporation Pvt. Ltd. (India), Ekran System (U.S.), Simeio (U.S.), Imprivata, Inc. (U.S.), Amazon Web Services, Inc. (U.S.), Microsoft (U.S.), OneLogin (U.S.), Salesforce, Inc. (U.S.), Broadcom (U.S.), Splashtop Inc. (U.S.), Oracle (U.S.), HashiCorp (U.S.), IBM Corporation (U.S.), and Saviynt Inc. (U.S.) |
| By Region |
|
privileged access management (PAM) solutions Market Trends
The global market for privileged access management (PAM) solutions is witnessing a dynamic change owing to the growing need for advanced security measures in the face of ever-increasing cyber security threats, including data leakage and hacking attempts. Companies are beginning to understand the need to protect their sensitive data and core functionalities; therefore, the monitoring and management of privileged users has risen significantly. This is also because of the need for regulatory compliance, whereby, for example, firms have to follow strict measures on accessing and protecting data from unauthorised parties. This has led most organisations to embrace PAM solutions to be able to have fine-grained access control, accountability, and insider threat protection. A further development worth mentioning in the PAM market is the use of some of the new technologies like artificial intelligence (AI) and machine learning (ML) and their deployment within the PAM solutions. These technologies augment the functionalities of PAM systems by providing the capability of instantaneous identification of threats alongside their elimination in an autonomous way. On a different note, the increase in the trend of working from home and the uptake of cloud services has made organisations go for PAM solutions that are hybrid and allow the control of access to resources in the cloud and on-premises.privileged access management (PAM) solutions Market Leading Players
The key players profiled in the report are BeyondTrust Corporation (U.S.), CyberArk Software Ltd. (U.S.), SecureAuth Corporation (U.S.), One Identity LLC (U.S.), Zoho Corporation Pvt. Ltd. (India), Ekran System (U.S.), Simeio (U.S.), Imprivata, Inc. (U.S.), Amazon Web Services, Inc. (U.S.), Microsoft (U.S.), OneLogin (U.S.), Salesforce, Inc. (U.S.), Broadcom (U.S.), Splashtop Inc. (U.S.), Oracle (U.S.), HashiCorp (U.S.), IBM Corporation (U.S.), and Saviynt Inc. (U.S.)Growth Accelerators
The main reason behind the privileged access management (PAM) solutions market is the sophistication and frequency of cyber threats against organisations' sensitive data and critical systems. As businesses increasingly migrate to digital formats and move to cloud-based environments, security of the delicate account becomes paramount. PAM solutions enforce strong access controls and monitor user activity with strict restrictions, thereby maintaining robust cybersecurity posture for the organisations concerned. This added demand comes from regulatory compliance requirements as various industries are compelled to adopt extremely stringent access management protocols in place to safeguard their data. Another key market driver for the PAM solutions market is the rising awareness of insider threats and the management of effective control over the risks within as well as external to the organization. Firms are becoming more aware of the fact that privileged accounts carry much greater risk since the level of access they carry, and such accounts are always preferred targets for nefarious actors or even accidentally mistaken access by legitimate users. With the increasing adoption of the zero-trust security model along with the principle of least privilege for access, PAM solutions now rely mostly on ensuring that users are restricted from accessing only that which is needed to complete the job.privileged access management (PAM) solutions Market Segmentation analysis
The Global privileged access management (PAM) solutions is segmented by Type, Application, and Region. By Type, the market is divided into Distributed Software, Physical Appliance, Virtual Appliance . The Application segment categorizes the market based on its usage such as Windows, Unix and Linux, Mac OS, Infrastructure Devices, IoT. Geographically, the market is assessed across key Regions like North America(United States, Canada, Mexico), South America(Brazil, Argentina, Chile, Rest of South America), Europe(Germany, France, Italy, United Kingdom, Benelux, Nordics, Rest of Europe), Asia Pacific(China, Japan, India, South Korea, Australia, Southeast Asia, Rest of Asia-Pacific), MEA(Middle East, Africa) and others, each presenting distinct growth opportunities and challenges influenced by the regions.Competitive Landscape
In the privileged access management (PAM) solutions market, there are multiple established players as well as some emerging start-ups competing to deliver the best strategies for controlling and overseeing access to critical infrastructure and sensitive information. The companies that fall within this category include some of the following: CyberArk, BeyondTrust, and Thycotic, among others, have all developed and designed inventive and sophisticated PAM capable of credential management, session history, and threat management. They have developed new capabilities and new strategies to fight modern cyber threats, which include the use of cutting-edge technologies such as AI and machine learning. Rather than just the traditional vendors, PAM is also witnessing a rise in demand for vendor solutions such as those offered by Microsoft, IBM, and Okta, which are essentially PAM embedded within an identity access management system. This exemplifies the growing need for integration and growth because of the remote working environment and the need for digitalisation.Challenges In privileged access management (PAM) solutions Market
The market for privileged access management (PAM) solutions is maturing, but integration with manufacturing processes remains a challenge. Most organisations contain legacy and new systems, which add further difficulty to the implementation of PAM solutions. This complexity in regard to integration often causes lengthened deployment schedules and raised expenses, which threatens to disrupt smooth business operations. Moreover, adoption of changes, including those pertaining to PAM systems, may meet strong resistance from personnel used to operating within established processes. This challenge is not limited to the competitive landscape itself but, in fact, extends further, as it affects the product development as well. Every other day, there are such innovations in the presentation and use of attacks on privileged account users that the management of such systems cannot just sit back and develop the best product on the market. That is why PAM solutions can be found in every gouging-out resource. This demands heavy investment as far as language technology is concerned, drastically affecting the profitability of all the players.Risks & Prospects in privileged access management (PAM) solutions Market
The market for privileged access management (PAM) solutions is poised for growth and expansion owing to, among other things, the increasing rate of cyber threats and data security concerns that are becoming common in many sectors. Due to the heightened understanding by organisations of the dangers posed by granting unauthorised individuals access to confidential data, the need for effective PAM solutions is increasing. These solutions assist companies in managing and controlling the use of privileged accounts, tracking user behaviour, and meeting the needed standards. This encourages the stakeholders to engage in corporate innovation by designing the entire range of PAM solutions tailored to various organisational requirements, including but not limited to managing identities and threat prevention control. Moreover, the emergence of cloud services and hybrid IT environments has created a conducive environment for the growth of PAM markets. As organisations are shifting into cloud-based infrastructures, managing and protecting privileged access consists of more challenges, propelling the necessity of PAM solutions the other way around. Vendors can take advantage of this opportunity by creating cloud-native PAM solutions that incorporate scaling, flexibility, and integration with the current security management systems.Key Target Audience
The major focus of the market for privileged access management solution providers is on businesses operating in various sectors, including finance, health care, and technology, that value confidentiality and integrity of sensitive data and critical systems. These organisations are more adopting PAM solutions to oversee the system’s highly privileged accounts, which only allow access to performed functions by authorised users. Through PAM, organisations reduce the risk of data losses, follow legal requirements and policies, and protect their IT environments.,, Another important component is made up of IT security teams or professionals whose duty is to protect the digital resources of the organisation. This audience incorporates cybersecurity analysts, network administrators, and compliance officers who look for better PAM solution packages to improve their security and cut back on the processes of access management. This user base is essential because as the threats posed by cyber criminals become more advanced and the laws governing these criminals change, this group assists in the promotion and use of PAM systems, allowing the stable development of security systems and user management in the organisation’s network.Merger and acquisition
The privileged access management (PAM) solutions market is on a growth path, but coupling these solutions with manufacturing processes seems to be a challenge. Most organisations have old and new systems, which also complicates the implementation of PAM solutions. This is the factor that creates challenges in the integration process most of the time, resulting in delays in deployment and incurring extra costs that may hinder the normal running of the business. In addition, changes, including those associated with PAM systems, may be fiercely opposed by employees who are accustomed to functioning in certain ways. This predicament is not confined solely to the realm of rivalry; rather, it goes beyond this as it impacts the very creation of the goods as well. It seems that innovations in the presentation and the attack methods against privileged account users appear on the business every other day, and therefore the management of such systems cannot afford to remain in the market, only aiming at producing the best product. That is why corporations like these have to invest in every other resource with great financial costs. This is rather a burdensome action, especially in regard to language technology, which reduces the overall profit of every participant in the existing market.- 1.1 Report description
- 1.2 Key market segments
- 1.3 Key benefits to the stakeholders
2: Executive Summary
- 2.1 privileged access management (PAM) solutions- Snapshot
- 2.2 privileged access management (PAM) solutions- Segment Snapshot
- 2.3 privileged access management (PAM) solutions- Competitive Landscape Snapshot
3: Market Overview
- 3.1 Market definition and scope
- 3.2 Key findings
- 3.2.1 Top impacting factors
- 3.2.2 Top investment pockets
- 3.3 Porter’s five forces analysis
- 3.3.1 Low bargaining power of suppliers
- 3.3.2 Low threat of new entrants
- 3.3.3 Low threat of substitutes
- 3.3.4 Low intensity of rivalry
- 3.3.5 Low bargaining power of buyers
- 3.4 Market dynamics
- 3.4.1 Drivers
- 3.4.2 Restraints
- 3.4.3 Opportunities
4: privileged access management (PAM) solutions Market by Type
- 4.1 Overview
- 4.1.1 Market size and forecast
- 4.2 Software
- 4.2.1 Key market trends, factors driving growth, and opportunities
- 4.2.2 Market size and forecast, by region
- 4.2.3 Market share analysis by country
- 4.3 Physical Appliance
- 4.3.1 Key market trends, factors driving growth, and opportunities
- 4.3.2 Market size and forecast, by region
- 4.3.3 Market share analysis by country
- 4.4 Virtual Appliance
- 4.4.1 Key market trends, factors driving growth, and opportunities
- 4.4.2 Market size and forecast, by region
- 4.4.3 Market share analysis by country
5: privileged access management (PAM) solutions Market by Application / by End Use
- 5.1 Overview
- 5.1.1 Market size and forecast
- 5.2 Windows
- 5.2.1 Key market trends, factors driving growth, and opportunities
- 5.2.2 Market size and forecast, by region
- 5.2.3 Market share analysis by country
- 5.3 Unix and Linux
- 5.3.1 Key market trends, factors driving growth, and opportunities
- 5.3.2 Market size and forecast, by region
- 5.3.3 Market share analysis by country
- 5.4 Mac OS
- 5.4.1 Key market trends, factors driving growth, and opportunities
- 5.4.2 Market size and forecast, by region
- 5.4.3 Market share analysis by country
- 5.5 Infrastructure Devices
- 5.5.1 Key market trends, factors driving growth, and opportunities
- 5.5.2 Market size and forecast, by region
- 5.5.3 Market share analysis by country
- 5.6 IoT
- 5.6.1 Key market trends, factors driving growth, and opportunities
- 5.6.2 Market size and forecast, by region
- 5.6.3 Market share analysis by country
6: privileged access management (PAM) solutions Market by End Use
- 6.1 Overview
- 6.1.1 Market size and forecast
- 6.2 IT and Telecom
- 6.2.1 Key market trends, factors driving growth, and opportunities
- 6.2.2 Market size and forecast, by region
- 6.2.3 Market share analysis by country
- 6.3 Healthcare
- 6.3.1 Key market trends, factors driving growth, and opportunities
- 6.3.2 Market size and forecast, by region
- 6.3.3 Market share analysis by country
- 6.4 Energy and Utility
- 6.4.1 Key market trends, factors driving growth, and opportunities
- 6.4.2 Market size and forecast, by region
- 6.4.3 Market share analysis by country
- 6.5 Retail
- 6.5.1 Key market trends, factors driving growth, and opportunities
- 6.5.2 Market size and forecast, by region
- 6.5.3 Market share analysis by country
- 6.6 Manufacturing
- 6.6.1 Key market trends, factors driving growth, and opportunities
- 6.6.2 Market size and forecast, by region
- 6.6.3 Market share analysis by country
- 6.7 Government and Defense
- 6.7.1 Key market trends, factors driving growth, and opportunities
- 6.7.2 Market size and forecast, by region
- 6.7.3 Market share analysis by country
- 6.8 Others
- 6.8.1 Key market trends, factors driving growth, and opportunities
- 6.8.2 Market size and forecast, by region
- 6.8.3 Market share analysis by country
7: privileged access management (PAM) solutions Market by Region
- 7.1 Overview
- 7.1.1 Market size and forecast By Region
- 7.2 North America
- 7.2.1 Key trends and opportunities
- 7.2.2 Market size and forecast, by Type
- 7.2.3 Market size and forecast, by Application
- 7.2.4 Market size and forecast, by country
- 7.2.4.1 United States
- 7.2.4.1.1 Key market trends, factors driving growth, and opportunities
- 7.2.4.1.2 Market size and forecast, by Type
- 7.2.4.1.3 Market size and forecast, by Application
- 7.2.4.2 Canada
- 7.2.4.2.1 Key market trends, factors driving growth, and opportunities
- 7.2.4.2.2 Market size and forecast, by Type
- 7.2.4.2.3 Market size and forecast, by Application
- 7.2.4.3 Mexico
- 7.2.4.3.1 Key market trends, factors driving growth, and opportunities
- 7.2.4.3.2 Market size and forecast, by Type
- 7.2.4.3.3 Market size and forecast, by Application
- 7.2.4.1 United States
- 7.3 South America
- 7.3.1 Key trends and opportunities
- 7.3.2 Market size and forecast, by Type
- 7.3.3 Market size and forecast, by Application
- 7.3.4 Market size and forecast, by country
- 7.3.4.1 Brazil
- 7.3.4.1.1 Key market trends, factors driving growth, and opportunities
- 7.3.4.1.2 Market size and forecast, by Type
- 7.3.4.1.3 Market size and forecast, by Application
- 7.3.4.2 Argentina
- 7.3.4.2.1 Key market trends, factors driving growth, and opportunities
- 7.3.4.2.2 Market size and forecast, by Type
- 7.3.4.2.3 Market size and forecast, by Application
- 7.3.4.3 Chile
- 7.3.4.3.1 Key market trends, factors driving growth, and opportunities
- 7.3.4.3.2 Market size and forecast, by Type
- 7.3.4.3.3 Market size and forecast, by Application
- 7.3.4.4 Rest of South America
- 7.3.4.4.1 Key market trends, factors driving growth, and opportunities
- 7.3.4.4.2 Market size and forecast, by Type
- 7.3.4.4.3 Market size and forecast, by Application
- 7.3.4.1 Brazil
- 7.4 Europe
- 7.4.1 Key trends and opportunities
- 7.4.2 Market size and forecast, by Type
- 7.4.3 Market size and forecast, by Application
- 7.4.4 Market size and forecast, by country
- 7.4.4.1 Germany
- 7.4.4.1.1 Key market trends, factors driving growth, and opportunities
- 7.4.4.1.2 Market size and forecast, by Type
- 7.4.4.1.3 Market size and forecast, by Application
- 7.4.4.2 France
- 7.4.4.2.1 Key market trends, factors driving growth, and opportunities
- 7.4.4.2.2 Market size and forecast, by Type
- 7.4.4.2.3 Market size and forecast, by Application
- 7.4.4.3 Italy
- 7.4.4.3.1 Key market trends, factors driving growth, and opportunities
- 7.4.4.3.2 Market size and forecast, by Type
- 7.4.4.3.3 Market size and forecast, by Application
- 7.4.4.4 United Kingdom
- 7.4.4.4.1 Key market trends, factors driving growth, and opportunities
- 7.4.4.4.2 Market size and forecast, by Type
- 7.4.4.4.3 Market size and forecast, by Application
- 7.4.4.5 Benelux
- 7.4.4.5.1 Key market trends, factors driving growth, and opportunities
- 7.4.4.5.2 Market size and forecast, by Type
- 7.4.4.5.3 Market size and forecast, by Application
- 7.4.4.6 Nordics
- 7.4.4.6.1 Key market trends, factors driving growth, and opportunities
- 7.4.4.6.2 Market size and forecast, by Type
- 7.4.4.6.3 Market size and forecast, by Application
- 7.4.4.7 Rest of Europe
- 7.4.4.7.1 Key market trends, factors driving growth, and opportunities
- 7.4.4.7.2 Market size and forecast, by Type
- 7.4.4.7.3 Market size and forecast, by Application
- 7.4.4.1 Germany
- 7.5 Asia Pacific
- 7.5.1 Key trends and opportunities
- 7.5.2 Market size and forecast, by Type
- 7.5.3 Market size and forecast, by Application
- 7.5.4 Market size and forecast, by country
- 7.5.4.1 China
- 7.5.4.1.1 Key market trends, factors driving growth, and opportunities
- 7.5.4.1.2 Market size and forecast, by Type
- 7.5.4.1.3 Market size and forecast, by Application
- 7.5.4.2 Japan
- 7.5.4.2.1 Key market trends, factors driving growth, and opportunities
- 7.5.4.2.2 Market size and forecast, by Type
- 7.5.4.2.3 Market size and forecast, by Application
- 7.5.4.3 India
- 7.5.4.3.1 Key market trends, factors driving growth, and opportunities
- 7.5.4.3.2 Market size and forecast, by Type
- 7.5.4.3.3 Market size and forecast, by Application
- 7.5.4.4 South Korea
- 7.5.4.4.1 Key market trends, factors driving growth, and opportunities
- 7.5.4.4.2 Market size and forecast, by Type
- 7.5.4.4.3 Market size and forecast, by Application
- 7.5.4.5 Australia
- 7.5.4.5.1 Key market trends, factors driving growth, and opportunities
- 7.5.4.5.2 Market size and forecast, by Type
- 7.5.4.5.3 Market size and forecast, by Application
- 7.5.4.6 Southeast Asia
- 7.5.4.6.1 Key market trends, factors driving growth, and opportunities
- 7.5.4.6.2 Market size and forecast, by Type
- 7.5.4.6.3 Market size and forecast, by Application
- 7.5.4.7 Rest of Asia-Pacific
- 7.5.4.7.1 Key market trends, factors driving growth, and opportunities
- 7.5.4.7.2 Market size and forecast, by Type
- 7.5.4.7.3 Market size and forecast, by Application
- 7.5.4.1 China
- 7.6 MEA
- 7.6.1 Key trends and opportunities
- 7.6.2 Market size and forecast, by Type
- 7.6.3 Market size and forecast, by Application
- 7.6.4 Market size and forecast, by country
- 7.6.4.1 Middle East
- 7.6.4.1.1 Key market trends, factors driving growth, and opportunities
- 7.6.4.1.2 Market size and forecast, by Type
- 7.6.4.1.3 Market size and forecast, by Application
- 7.6.4.2 Africa
- 7.6.4.2.1 Key market trends, factors driving growth, and opportunities
- 7.6.4.2.2 Market size and forecast, by Type
- 7.6.4.2.3 Market size and forecast, by Application
- 7.6.4.1 Middle East
- 8.1 Overview
- 8.2 Key Winning Strategies
- 8.3 Top 10 Players: Product Mapping
- 8.4 Competitive Analysis Dashboard
- 8.5 Market Competition Heatmap
- 8.6 Leading Player Positions, 2022
9: Company Profiles
- 9.1 BeyondTrust Corporation (U.S.)
- 9.1.1 Company Overview
- 9.1.2 Key Executives
- 9.1.3 Company snapshot
- 9.1.4 Active Business Divisions
- 9.1.5 Product portfolio
- 9.1.6 Business performance
- 9.1.7 Major Strategic Initiatives and Developments
- 9.2 CyberArk Software Ltd. (U.S.)
- 9.2.1 Company Overview
- 9.2.2 Key Executives
- 9.2.3 Company snapshot
- 9.2.4 Active Business Divisions
- 9.2.5 Product portfolio
- 9.2.6 Business performance
- 9.2.7 Major Strategic Initiatives and Developments
- 9.3 SecureAuth Corporation (U.S.)
- 9.3.1 Company Overview
- 9.3.2 Key Executives
- 9.3.3 Company snapshot
- 9.3.4 Active Business Divisions
- 9.3.5 Product portfolio
- 9.3.6 Business performance
- 9.3.7 Major Strategic Initiatives and Developments
- 9.4 One Identity LLC (U.S.)
- 9.4.1 Company Overview
- 9.4.2 Key Executives
- 9.4.3 Company snapshot
- 9.4.4 Active Business Divisions
- 9.4.5 Product portfolio
- 9.4.6 Business performance
- 9.4.7 Major Strategic Initiatives and Developments
- 9.5 Zoho Corporation Pvt. Ltd. (India)
- 9.5.1 Company Overview
- 9.5.2 Key Executives
- 9.5.3 Company snapshot
- 9.5.4 Active Business Divisions
- 9.5.5 Product portfolio
- 9.5.6 Business performance
- 9.5.7 Major Strategic Initiatives and Developments
- 9.6 Ekran System (U.S.)
- 9.6.1 Company Overview
- 9.6.2 Key Executives
- 9.6.3 Company snapshot
- 9.6.4 Active Business Divisions
- 9.6.5 Product portfolio
- 9.6.6 Business performance
- 9.6.7 Major Strategic Initiatives and Developments
- 9.7 Simeio (U.S.)
- 9.7.1 Company Overview
- 9.7.2 Key Executives
- 9.7.3 Company snapshot
- 9.7.4 Active Business Divisions
- 9.7.5 Product portfolio
- 9.7.6 Business performance
- 9.7.7 Major Strategic Initiatives and Developments
- 9.8 Imprivata
- 9.8.1 Company Overview
- 9.8.2 Key Executives
- 9.8.3 Company snapshot
- 9.8.4 Active Business Divisions
- 9.8.5 Product portfolio
- 9.8.6 Business performance
- 9.8.7 Major Strategic Initiatives and Developments
- 9.9 Inc. (U.S.)
- 9.9.1 Company Overview
- 9.9.2 Key Executives
- 9.9.3 Company snapshot
- 9.9.4 Active Business Divisions
- 9.9.5 Product portfolio
- 9.9.6 Business performance
- 9.9.7 Major Strategic Initiatives and Developments
- 9.10 Amazon Web Services
- 9.10.1 Company Overview
- 9.10.2 Key Executives
- 9.10.3 Company snapshot
- 9.10.4 Active Business Divisions
- 9.10.5 Product portfolio
- 9.10.6 Business performance
- 9.10.7 Major Strategic Initiatives and Developments
- 9.11 Inc. (U.S.)
- 9.11.1 Company Overview
- 9.11.2 Key Executives
- 9.11.3 Company snapshot
- 9.11.4 Active Business Divisions
- 9.11.5 Product portfolio
- 9.11.6 Business performance
- 9.11.7 Major Strategic Initiatives and Developments
- 9.12 Microsoft (U.S.)
- 9.12.1 Company Overview
- 9.12.2 Key Executives
- 9.12.3 Company snapshot
- 9.12.4 Active Business Divisions
- 9.12.5 Product portfolio
- 9.12.6 Business performance
- 9.12.7 Major Strategic Initiatives and Developments
- 9.13 OneLogin (U.S.)
- 9.13.1 Company Overview
- 9.13.2 Key Executives
- 9.13.3 Company snapshot
- 9.13.4 Active Business Divisions
- 9.13.5 Product portfolio
- 9.13.6 Business performance
- 9.13.7 Major Strategic Initiatives and Developments
- 9.14 Salesforce
- 9.14.1 Company Overview
- 9.14.2 Key Executives
- 9.14.3 Company snapshot
- 9.14.4 Active Business Divisions
- 9.14.5 Product portfolio
- 9.14.6 Business performance
- 9.14.7 Major Strategic Initiatives and Developments
- 9.15 Inc. (U.S.)
- 9.15.1 Company Overview
- 9.15.2 Key Executives
- 9.15.3 Company snapshot
- 9.15.4 Active Business Divisions
- 9.15.5 Product portfolio
- 9.15.6 Business performance
- 9.15.7 Major Strategic Initiatives and Developments
- 9.16 Broadcom (U.S.)
- 9.16.1 Company Overview
- 9.16.2 Key Executives
- 9.16.3 Company snapshot
- 9.16.4 Active Business Divisions
- 9.16.5 Product portfolio
- 9.16.6 Business performance
- 9.16.7 Major Strategic Initiatives and Developments
- 9.17 Splashtop Inc. (U.S.)
- 9.17.1 Company Overview
- 9.17.2 Key Executives
- 9.17.3 Company snapshot
- 9.17.4 Active Business Divisions
- 9.17.5 Product portfolio
- 9.17.6 Business performance
- 9.17.7 Major Strategic Initiatives and Developments
- 9.18 Oracle (U.S.)
- 9.18.1 Company Overview
- 9.18.2 Key Executives
- 9.18.3 Company snapshot
- 9.18.4 Active Business Divisions
- 9.18.5 Product portfolio
- 9.18.6 Business performance
- 9.18.7 Major Strategic Initiatives and Developments
- 9.19 HashiCorp (U.S.)
- 9.19.1 Company Overview
- 9.19.2 Key Executives
- 9.19.3 Company snapshot
- 9.19.4 Active Business Divisions
- 9.19.5 Product portfolio
- 9.19.6 Business performance
- 9.19.7 Major Strategic Initiatives and Developments
- 9.20 IBM Corporation (U.S.)
- 9.20.1 Company Overview
- 9.20.2 Key Executives
- 9.20.3 Company snapshot
- 9.20.4 Active Business Divisions
- 9.20.5 Product portfolio
- 9.20.6 Business performance
- 9.20.7 Major Strategic Initiatives and Developments
- 9.21 and Saviynt Inc. (U.S.)
- 9.21.1 Company Overview
- 9.21.2 Key Executives
- 9.21.3 Company snapshot
- 9.21.4 Active Business Divisions
- 9.21.5 Product portfolio
- 9.21.6 Business performance
- 9.21.7 Major Strategic Initiatives and Developments
10: Analyst Perspective and Conclusion
- 10.1 Concluding Recommendations and Analysis
- 10.2 Strategies for Market Potential
Scope of Report
| Aspects | Details |
|---|---|
By Type |
|
By Application |
|
By End Use |
|
Report Licenses
Our Team

Frequently Asked Questions (FAQ):
What is the estimated market size of privileged access management (PAM) solutions in 2030?
+
-
What is the growth rate of privileged access management (PAM) solutions Market?
+
-
What are the latest trends influencing the privileged access management (PAM) solutions Market?
+
-
Who are the key players in the privileged access management (PAM) solutions Market?
+
-
How is the privileged access management (PAM) solutions } industry progressing in scaling its end-use implementations?
+
-
What product types are analyzed in the privileged access management (PAM) solutions Market Study?
+
-
What geographic breakdown is available in Global privileged access management (PAM) solutions Market Study?
+
-
Which region holds the second position by market share in the privileged access management (PAM) solutions market?
+
-
How are the key players in the privileged access management (PAM) solutions market targeting growth in the future?
+
-
What are the opportunities for new entrants in the privileged access management (PAM) solutions market?
+
-

